In January 2019, I started a series of articles that documented the creation of our Modern IT Ecosystem.
The articles predominantly focused on the architecture, technology and positioning of key capabilities, but also (where appropriate) referenced facilitating processes and methodologies.
Up to now, I have written twelve articles (listed below), covering a wide range of topics. Although each article covers a specific area, they are best reviewed in order, starting with “Greenfield Opportunity”, which provides the required.
- Part One: Greenfield Opportunity
- Part Two: Modern IT Ecosystem
- Part Three: Service Delivery
- Part Four: SD-WAN
- Part Five: Hybrid Multi-Cloud
- Part Six: Automation
- Part Seven: Device-as-a-Service
- Part Eight: Identity Access Management
- Part Nine: Unified Communications
- Part Ten: Line of Business Apps
- Part Eleven: Architecture Community
- Part Twelve: O365 Tenant Migration
- Part Thirteen: Data Protection
- Part Fourteen: SIAM
- Part Fifteen: IT Ecosystem
This final article (part fifteen) aims to conclude the series (at least for now), provides a summary of the decisions, which contributed to our vision of a Modern IT Ecosystem.
Modern IT Ecosystem
In the article “Modern IT Ecosystem”, I shared the following “marchitecture” diagram, which I aimed to highlight my desired end-state.
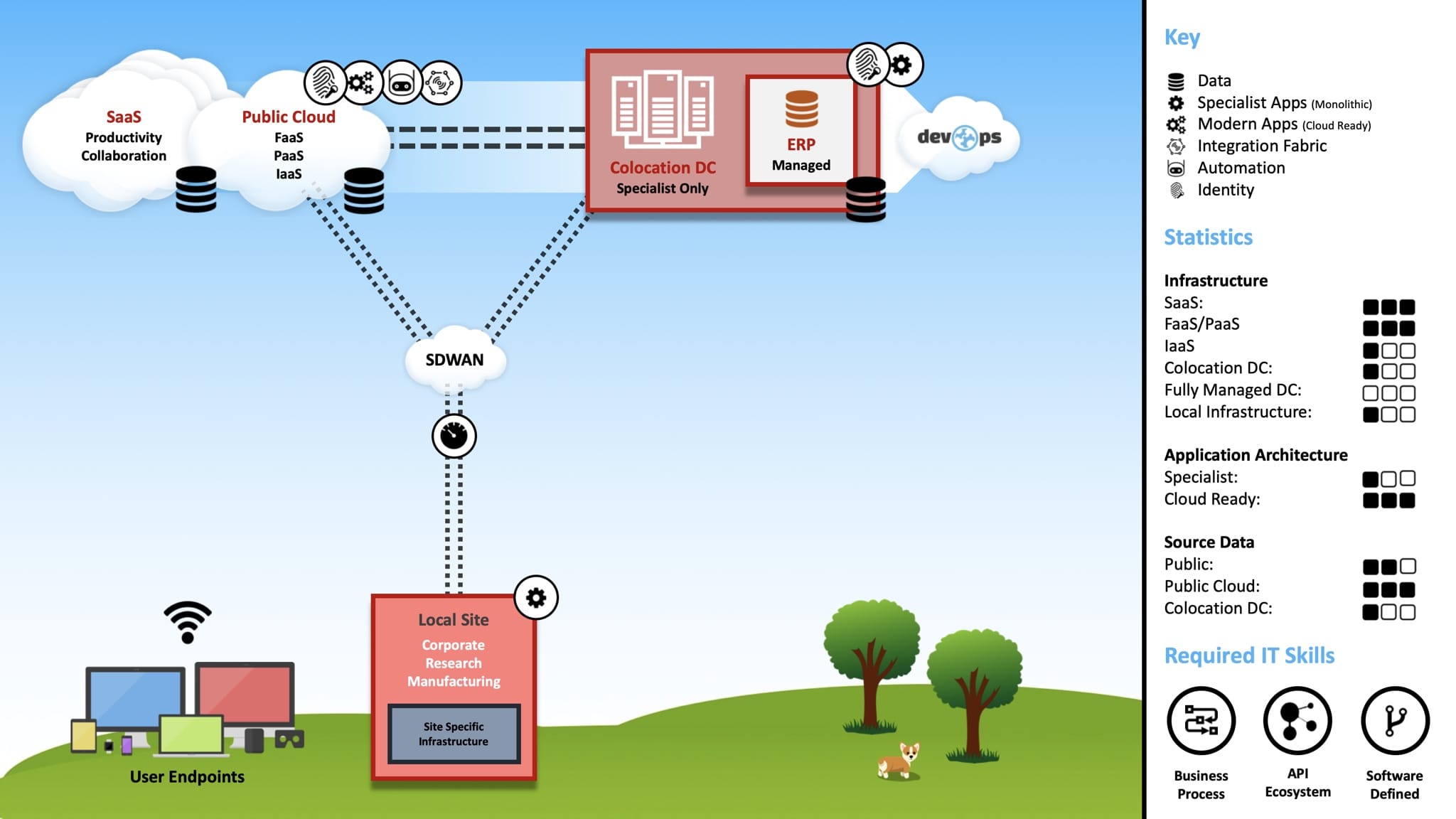
Throughout the past year, we have essentially populated this diagram, detailing the architecture, positioning technologies, as well as highlighting the dependencies and facilitating processes.
The diagram below acts as a conclusion, overlaying the technologies and vendors that we have positioned throughout the series. The details and rationale for each decision can be found within the individual articles.
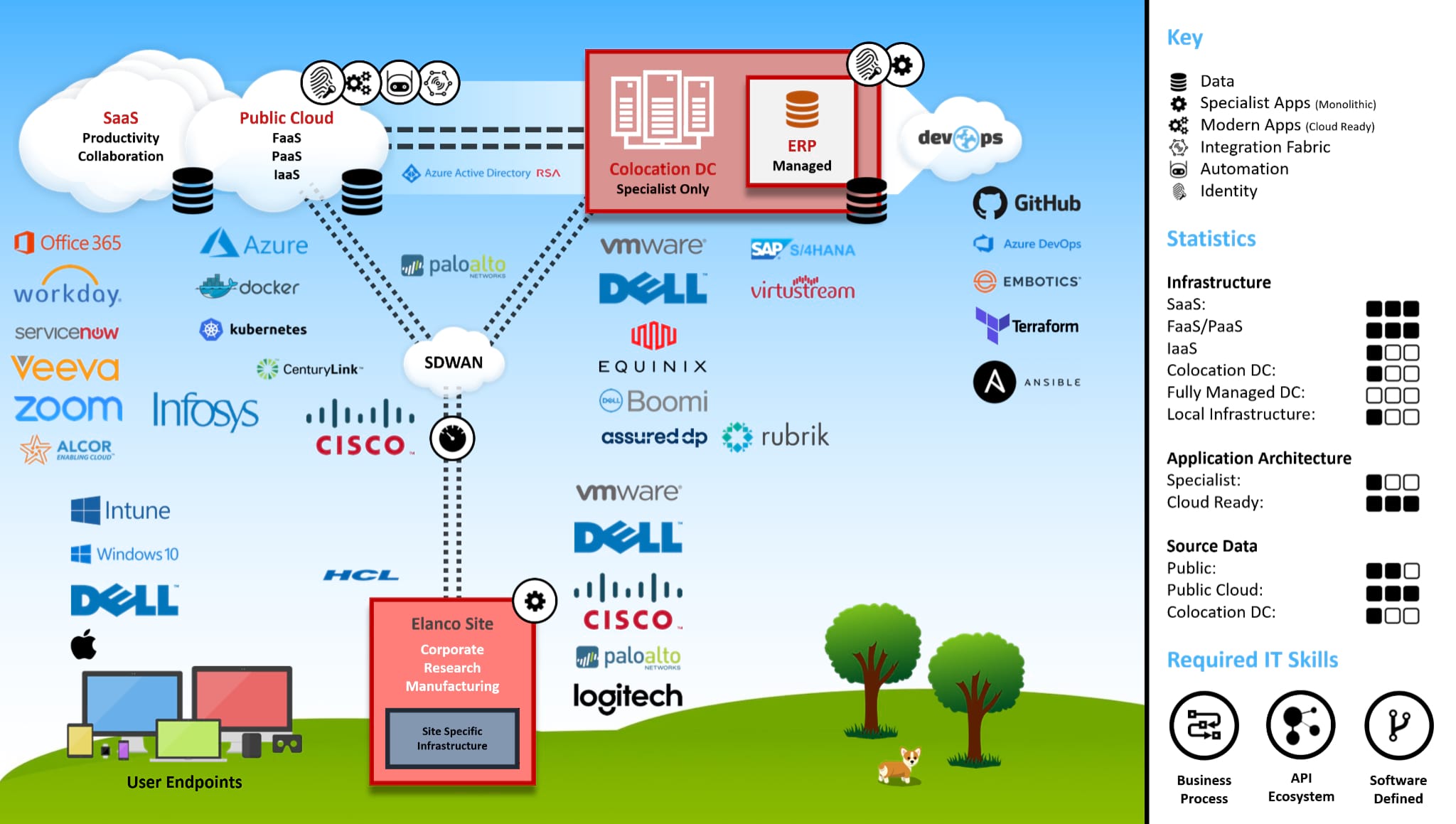
As you can see from the diagram, a modern IT ecosystem can quickly become a complex landscape, supported by a wide range of technologies and vendors. With that said, I believe the philosophy, principles and declarations outlined in the article “Modern IT Ecosystem” provided a strong foundation for decision making, helping to drive synergy, improve efficiency and reduce technical debt.
Although I feel confident about our proposed architecture, there are many areas and details I simply did not have the time to document. For example, areas such as Domain Name Service (DNS) provider, Public Key Infrastructure (PKI), Privileged Access Management (PAM), etc. These areas (alongside many others) support critical capabilities that must exist to enable a secure, scalable IT ecosystem.
It is also worth noting that a lot can change within a year, therefore technologies positioned as part of my proposed “modern” IT ecosystem have already been superseded, etc. For example, we have positioned RSA Identity Governance and Access (IGL) as part of my proposed Identity Access Management architecture. Although still a perfectly viable option, part of our decision was driven by the desire to maximise the investment with Dell Technologies. In February 2020, Dell Technologies announced their intent to divest RSA, which reduces the value proposition associated with the decision.
Cloud is another area that continues to evolve quickly, with new capabilities being added at a furious pace. For example, Microsoft continues to expand and enhance services within Office 365 and Azure, which could potentially be used to replace third-party solutions, enabling a better user experience and reducing costs (especially if bundled under the Microsoft 365 E5 License).
Conclusion
I do not claim that our proposed architecture is authoritative (there is an infinite number of options), especially considering the vast number of unknowns at the start of our journey.
With that said, I believe this series has accomplished the goal of documenting a robust and highly flexible IT ecosystem for a traditional enterprise business, with emerging digital business opportunities.
For example, prioritising modern technologies and techniques, such as the use of Public Cloud, following an API-Centric Architecture that is Software-Defined and highly automated. This positioning, combined with pragmatic architecture decisions (e.g. Colocation Data Centres) help ensure the proposed IT ecosystem could support almost any workload (legacy or modern).
Finally, it is important to recognise that although this series has predominantly focused on architecture, this is only one piece of the puzzle, with the processes, methodologies and organisation design being critical when looking to unlock the total value proposition. I covered a few of these areas, but would likely need to write a separate series to provide the required level of detail (maybe something for the future).
